CH-1 INTRODUCTION TO COMPUTER NETWORK
I. FILL IN THE BLANKS
1. The hostname command is used to display —————
Ans: name of the computer.
2. The length of a IPv4 and a IPv6 is ——— and ——— bytes respectively.
Ans:32 bit ; 128 bit
3. An access point is used to connect ——–
Ans: wireless network
4. The ping command is used to ——–
Ans: verify the connectivity between two computers
5. HTTPS transfer ———- data.
Ans: encrypted
II. MULTIPLE CHOICE QUESTIONS:
1. Which device is required to connect multiple heterogeneous networks?
A) Hub B) Switch C) Router D) Access Point
Ans: C) Router
2. Which is the largest type of computer network?
A) PAN B) LAN C) MAN D) WAN
Ans: D) WAN
3. Which protocol transfers encrypted data instead of plain data?
A) HTTP B) HTTPS C) FTP D) SMTP
Ans: B) HTTPS
4. How many bytes are reserved for OUI in a MAC address?
A) 3 B) 8 C) 24 D) 12
Ans: C) 24
5. IP address can be automatically assigned if the network is connected with
A) Access Point B) Mail Server C) Web Server D) DHCP Server
Ans: D) DHCP Server
III. SHORT ANSWER QUESTIONS
1. Mention the name of components required to set up a MAN network. Draw a block diagram of a MAN network labeling name of each component. (Hint: MAN network is a connection of multiple LAN)
Ans: A Metropolitan Area Network is formed by interconnecting multiple LANS that are within a limited geographic area. MANS typically merge the networks of multiple organizations to establish communication among them or to share common resources. Most of the time Internet Service Providers set up MAN to provide a high speed internet connection to multiple organizations. Most of the time the physical connection from one organization to another organization is established using Optical Fiber Cable to achieve good quality of service.
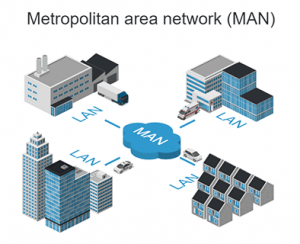
2. Why hostname should not be used to identify a computer in a computer network?
Ans: Although a hostname can be used to identify a computer in a computer network, hostnames may not be unique always. It means, there is a possibility that two or more computers in a computer network may have the same hostname.
There are options to change the hostname of a computer independently. If two or more users assign the same hostname to their computers intentionally or unintentionally, it is become difficult to identify a computer. Therefore, if the hostnames are not initialized centrally, the hostname should not be considered as a unique identifier of a computer in a computer network.
3. Give five examples of valid and five examples of invalid IPv4 addresses. (Hint: Each segment of an IPv4 address has a fixed length)
Ans: IP (version 4) addresses are 32-bit integers that can be expressed in hexadecimal notation. Its common format is x.x.x.x, where each x can be any value between 0 and 255.
Five valid IPv4 addresses:
172.16.254.1
172.16.254.2
192.0.2.146
192.150.2.146
19.0.211.146
Five invalid IPv4 addresses:
1.1.1 (only 3 decimal numbers
1.1.1. (ending with a dot)
1.1.1.x (containing an alphabet)
172.8.9.256 (decimal number exceeds 255)
172.8.-9.255 (negative decimal number)
4. Can we compare HTTP and FTP protocols? Mention their functionality.
Ans: The major difference between HTTP and FTP is that HTTP on request provides a web page from a web server to web browser. On the other hand, FTP is used to upload or download file between client and server.
5. How many 16 port switches are required to connect 31 computers in a network? (Hint: To connect all computers, all switches also should be connected among themselves)
Ans: Three 16 port switches are required to connect 31 computers in a network.
III. ADDITIONAL QUESTIONS & ANSWERS:
- Define encryption.
Ans: -Encryption is the process of converting information or data into a code, to prevent unauthorized access. Encrypted data can be again decrypted to get back the original data.
- what is the difference between HTTP and HTTPS?
Ans: – HTTP is a client-server protocol which means, a client requests a web resource using HTTP protocol and a web server provides that resource to the client.
The HTTPS (Hypertext Transfer Protocol Secure) is a combination of the Hypertext Transfer Protocol (HTTP) with added security features.
The main difference between HTTP and HTTPS is- in an HTTP communication data are sent without encryption, but in HTTPS, data are sent after encryption.
- What is Computer Network?
Ans: – A computer network is a set of computers and other units that are connected with each other. In a computer network, information or resources can be shared among connected computers. For example, if there is a printer connected to the network, that printer can be used by all computers of the network.
- What are the different types of Networks?
Ans: -The different types of Networks are as follows: –
- PAN (Personal Area Network)
- LAN (Local Area Network)
- MAN (Metropolitan Area Network)
- WAN (Wide Area Network)
4. Define the following: –
- PAN (Personal Area Network)
- LAN (Local Area Network)
- MAN (Metropolitan Area Network)
- WAN (Wide Area Network)
Ans:-
- PAN:- Personal Area Network is the simplest computer network. Personal Area Networks are normally set up for individual use within a limited geographical range. For example, someone can set up a Personal Area Network between his laptop and other electronic gadgets like a smartphone, PDA, tablet, printer, etc.
- LAN: – Local Area Network is the most commonly used network. In LAN, a number of units are connected to each other in a small area such as a building, office, etc. with the help of a common communication path like a switch or a similar connecting device.
- MAN: – A Metropolitan Area Network is formed by interconnecting multiple LANs that are within a limited geographic area. MANs typically merge the networks of multiple organizations to establish communication among them or to share common resources.
- WAN: – Wide Area Networks (WAN) are formed by connecting devices from multiple locations across the globe. Wide area networks are often established with Leased Telecommunication Circuits.
The Internet is an example of WAN since it is spared over the world.
- Explain in brief the comparison between different types of Computer Networks?
Ans:-
| PAN | LAN | MAN | WAN |
| PAN’s ownership is private Normally, one PAN is owned by a single person. | LAN ownership is private. i.e. everyone can create their LAN by connecting multiple devices. | MAN’s ownership may or may not be private. i.e. MAN may not be owned by one organization | WAN’s ownership is not private. Most of the time, WANs are owned by multiple organizations. |
| The data transfer rate of a PAN is very high. | The data transfer rate of a LAN is slower than PAN. | The data transfer rate of a MAN is slower than LAN.
|
The data transfer rate of a WAN is slower than MAN. |
| There is no congestion in PAN since data lines are not shared. | There may be a little congestion in LAN The congestion depends upon the number of communicating devices. | Normally the congestion in MAN is more than that of LAN. | In WAN, there is more congestion than MAN, LAN and PAN. |
| There is no design Issue in PAN and maintenance is easy. | LANs design and maintenance are easy. | MAN’s design and maintenance are more difficult than LAN. | WAN’s design and maintenance are more difficult than LAN as well as MAN. |
- What is Hostname?
Ans:- The hostname is the name of a computer or any connected device in a computer network. The hostname can be used to distinguish a device within a computer network.
- How can you change hostname of a computer on Windows and Linux?
Ans: – In windows 10 there is an option “Rename PC”. By navigating to this option, we can easily change the hostname of our Windows 10 computer.
In Linux operating system, there is a file “hostname” in the “/etc directory, which contains the hostname of the computer. To change the hostname of such system we have to modify the content of the file.
- Define IP Address and mention its uses?
Ans: – An Internet Protocol address (IP address) is a numerical label that is assigned to network devices to identify them uniquely.
IP addresses are the identifier that allows information to be sent between devices on a network: they contain location information and make devices accessible for communication.
- Can 2 devices have the same IP address?
Ans. An IP address conflict occurs when two or more devices on the same network are assigned the same IP address. Thus, no two devices can have the same IP address on one network.
- What is “IP conflict” error message?
Ans: – If one IP address is assigned so more than one computer, only one computer can establish the connection and the remaining computer shows an “IP conflict” error message. It means, to successfully connect a computer to a computer network, each computer must have a unique IP address.
- Briefly discuss the different types of IP address.
Ans:- There are two types of IP address-
Internet Protocol Version 4 (IPv4)-They are used to identify machines connected to a network. IPv4 is a 32-bit binary number. IPv4 addresses are separated by periods
Internet Protocol Version 6 (IPv6) They are used to identify machines connected to a network. IPv6 is a 128-bit binary number address. IPv6 addresses are separated by colons.
- What is MAC Address?
Ans: – MAC stands for Media Access Control. It is a unique identifier for network interfaces.
- Distinguish between IP address and MAC.
Ans. The IP address of a device mainly helps in identifying the connection of a network (using which the device is connecting to the network). The MAC Address, on the other hand, ensures the computer device’s physical location. It helps us to identify a given device on the available network uniquely.
- How do we write MAC address?
Ans. The MAC address is a 12-digit hexadecimal number that is most often displayed with a colon or hyphen separating every two digits (an octet), making it easier to read. example of MAC Address: 2C: 54:91:88: C9:E3
- Write the uses of hub and switch?
Ans: – A Hub is a networking device that connects other computer networking devices together. When a signal traverses a long distance, the strength of the signal decreases gradually. In such a situation, a hub can be used to act as a repeater which amplifies signals that deteriorate after traveling long distances over connecting cables.
A Switch is also a networking device that connects other computer networking devices, but Switches are generally more intelligent than hubs. A switch is a multiport device that is very much similar to a hub in appearance, but unlike hubs, a switch maintains some routing information about other network devices in the internal network.
- Write the difference between router and switch?
Ans:
| Router | Switch |
| The main objective of router is to connect various networks simultaneously.
|
While the main objective of switch is to connect various devices simultaneously.
|
| It works in network layer.
|
While it works in data link layer.
|
| Router is used by LAN as well as MAN.
|
While switch is used by only LAN.
|
| Through the router, data is sent in the form of packets.
|
While through switch data is sent in the form of frame.
|
18.What is Access point? Mention its functionality.
Ans: An access point is a network device that creates a wireless network. Computer or other devices that have a wireless network interface card can connect to such a wireless network.
The main functionality of the access point is to provide wireless network connectivity, some access point also has several ports to expand the network to support more wireless devices.
19.Define SSID.
Ans: A service set identifier is a sequence of characters that refers to a wireless local area network. To connect to a wireless network created by an Access Point, the user needs to know the SSID of the Access Point.
20.Define TCP, IP, POP, SMTP.
Ans: The TCP (Transmission Control Protocol) is a communication protocol that is primarily used for establishing communication between computers over a computer network. When data is sent over a network, the TCP in the source computer divides those data into a series of packets and sends those packets to the destination and the TCP at the destination reassembled them.
The IP (Internet Protocol) is mainly designed for addressing packets. The Internet Protocol is mostly used with TCP. The primary responsibility of Internet Protocol is to deliver packets from a source host to a destination host based on the IP address presents in a packet. TCP/IP is the broadly used protocol connecting computer networks.
POP stands for Post Office Protocol. The POP is designed for receiving incoming E-mails.
SMTP stands for Simple Mail Transfer Protocol. The SMTP is designed to send E-Mail.
21.What is FTP? Write its disadvantages.
Ans: The FTP (File Transfer Protocol) is a standard internet protocol used for transmitting files from one computer to another over a network. To transfer files using FTP protocol, one computer must allow the other computer to send or receive files.
The main disadvantage of FTP protocol is that it does not encrypt username, password, and data when logging in to the server and during data transfer.
22.What is SFTP and FTPS.
Ans: The main disadvantage of FTP protocol is that it does not encrypt username, password, and data when logging in to the server and during data transfer. To overcome this disadvantage two new protocols SFTP and FTPS were developed. SFTP and FTPS both protocol uses encryption and therefore it is considered as secure protocols to transfer files.
23.Define URL. Give an example.
Ans: URL stands for Uniform Resource Locator. URL is a locator or address that points to a specific website address.
E.G., https://sebahelp.com/
24.what is cloud storage.
Ans: cloud storage is normally a secure and ever-ready location that is held remotely.
25.What is ping command?
Ans: This is the most common networking command. This command is used to verify the connectivity between two computers. The syntax of the command is
ping <target host>
26.what is ipconfig?
Ans: The ipconfig command is used to determine your computer’s networking information, such as the IP address, address of its default gateway, etc.
27.What is arp command?
Ans: This command corresponds to the Address Resolution Protocol (ARP). ARP maps IP addresses to MAC addresses. The operating system maintains a list of such mapping in memory. Using the arp-a command we can display the list of IP addresses and their corresponding MAC addresses.
- Write the difference between POP & SMTP.
Ans: POP stands for Post Office Protocol. The POP is designed for receiving incoming E-mails.
SMTP stands for Simple Mail Transfer Protocol. The SMTP is designed to send E-Mail.
29.Write the full form of:
PAN: Personal area network
LAN: Local area network
MAN: Metropolitan area network
WAN: Wide area network
IP: Internet protocol
DHPC: Dynamic host configuration protocol
GUI: Graphical user interface
MAC: Media access control
NIC: Network interface card
OUI: Organizational unique identifier
SSID: Service set identifier
TCP: Transmission control protocol
POP: Post office protocol
SMTP: Simple mail transfer protocol
HTTP: Hypertext control protocol
HTTPS: Hypertext control protocol secure
FTP: File transfer protocol
URL: Uniform Resource Locator
====== END ======

